New Threat Alert: Tax-Themed Phishing Campaigns Leveraging PDFs, QR Codes, and Malware Delivery Platforms
Microsoft has issued a warning about a wave of new email phishing scams that use fake tax-related messages to trick people into revealing their login details or installing malware. These attacks are especially common during the U.S. tax season, when people are more likely to expect tax related emails or important documents.
The emails often contain PDF attachments or QR codes. When opened or scanned, they redirect users to legitimate looking websites such as DocuSign or Microsoft 365, but are actually designed to steal login details or secretly install malware.


Some of these emails use clever tricks to avoid being caught by security filters. For example, they use URL shorteners, hide links behind QR codes, or appear trustworthy by using well-known file-sharing services. In one case, attackers sent blank emails with an attached PDF containing a QR code leading to a fake Microsoft login page.
According to Microsoft, some of these scams are operated by ‘Storm-0249’, a cybercriminal group known for spreading dangerous software.
One campaign targeted U.S. residents with emails advising them to install a program that would allow hackers to control computers remotely, capture screenshots, and collect sensitive information.
These threats are part of a bigger trend. Microsoft and other security experts have recently seen more and more scams using:
Fraudulent websites to trick users into entering their login details
Compromised email tools (like MailChimp) to send scam messages
Fake websites and spoofed services like Adobe, Dropbox, and Spotify
Emails pretending to be security alerts or tax bills
These attacks target people in all kinds of industries—from IT and engineering to consulting—and are designed to look convincing, using familiar logos, names, and formats.
Microsoft recommends using phishing-resistant sign-in methods, updating their web browsers, and using security tools to proactively block suspicious activity before it reaches users.
https://thehackernews.com/2025/04/microsoft-warns-of-tax-themed-email.html
Blind Eagle APT Intensifies Cyberattacks on Colombian Government
A sophisticated cyber espionage and financial crime group known as Blind Eagle (APT-C-36) has ramped up attacks against Colombian government agencies and private sector organisations in a campaign dating back to November 2024. The threat actor, believed to operate primarily in Latin America, is known for its aggressive and persistent targeting of Colombian institutions, often focusing on government, finance, and law enforcement sectors.
Blind Eagle’s latest campaign leverages a vulnerability identified as CVE-2024-43451, which allows attackers to capture Windows NTLMv2 hashes, enabling credential theft and unauthorised access. Check Point researchers uncovered evidence that this exploit was actively used to infiltrate systems and establish persistent access to sensitive Colombian networks.
The group's attack chain includes:
Spear-phishing (or highly targeted) emails masquerading as legitimate government communications.
Malicious attachments that execute scripts to exploit the NTLMv2 vulnerability.
Credential harvesting from compromised networks to escalate privileges.
Deployment of Remote Access Trojans (RATs) for continued access and data exfiltration.
Blind Eagle is known for its rapid infection rates. One campaign in December 2024 affected over 1,600 victims, a significant number for a group that usually relies on highly targeted attacks.
Although Blind Eagle has long been associated with cyber espionage, researchers have noted that the group also engages in financially motivated attacks.
The attacks forced agencies to increase cybersecurity measures following disrupted government services, and raises concerns about data breaches. The Colombian government has urged rapid patching and security enhancements, but Blind Eagle continues to evolve its tactics, using new sophisticated techniques.
This campaign highlights the increasing cyber threats facing Latin American institutions, particularly from groups that combine espionage and financial motives. With Blind Eagle demonstrating an ability to rapidly compromise large numbers of victims, the need for proactive security measures has never been greater.
https://www.darkreading.com/cyberattacks-data-breaches/apt-blind-eagle-targets-colombian-government
Royal Mail Investigates Major Data Leak Linked to German Supplier Spectos
In early April 2025, Royal Mail began investigating a significant data breach after a hacker group named "GHNA" claimed to have leaked 144GB of sensitive information related to the company. The data, which includes over 16,000 files, reportedly contains customer names, addresses, package details, internal documents, and recordings of meetings between Royal Mail and its German supplier, Spectos GmbH, a third-party analytics and logistics software provider.
The breach appears to have originated from Spectos, who confirmed that its systems were compromised on March 29, 2025, leading to unauthorised access to customer-related data.
It is reported that the attackers exploited login credentials stolen in a 2021 malware incident involving a Spectos employee. These credentials may have also been used in a similar breach affecting Samsung Germany, where GHNA claimed to have accessed 270,000 customer service records. Royal Mail has stated that its own systems remain secure, with no disruption to postal services. The company is collaborating with Spectos to assess the breach’s impact and determine if any Royal Mail customer data was affected.
This incident underscores the risks associated with third-party vendors and the importance of robust cybersecurity measures across all partners in a supply chain.
https://www.theregister.com/2025/04/03/royal_mail_data_spectos/
Oracle Faces Lawsuit Over Alleged Cloud Data Breach Impacting Millions
In March 2025, Oracle Corporation was hit with a class-action lawsuit filed in Texas, following claims of a significant data breach affecting over 6 million users. A hacker known as “rose87168” alleged on Breach Forums that they obtained sensitive information such as encrypted passwords and user credentials. The hacker later released samples of this data online, which some cybersecurity experts, including CloudSEK, deemed authentic.
The lawsuit, initiated by Florida resident Michael Toikach, accuses Oracle of negligence and failing to promptly inform affected individuals. Toikach contends that his personal and health information was compromised through a healthcare provider using Oracle’s services, costing him considerable time monitoring his accounts for potential misuse.
Although Oracle has denied the breach, reports indicate that the company has quietly notified some healthcare clients about potential patient data exposure. The situation underscores the growing concerns over data security and the responsibilities of cloud service providers in protecting user information.
https://hackread.com/oracle-lawsuit-over-cloud-breach-affecting-millions/
WhatsApp for Windows Users Urged to Update Following Security Flaw in File Attachments
In April 2025, a security vulnerability was identified in WhatsApp's Windows desktop application , potentially allowing attackers to execute malicious code on users' computers. The flaw, designated as CVE-2025-30401, affects all versions of WhatsApp for Windows prior to 2.2450.6. This is due to the way WhatsApp handles file attachments: Attachments are displayed according to their MIME type (which indicates the nature of the file), but they are opened according to their file extension. This discrepancy means that a file appearing as a harmless image (such as a JPEG) could, in fact, be an executable program (like an .exe file) which could run malicious code on a user’s PC.
Meta, WhatsApp's parent company, acknowledged the issue and advised that an exploitation of this vulnerability requires the manual opening of the malicious attachment. While there is no confirmation of this flaw being actively exploited, security experts warn that users are often inclined to open attachments, especially if they appear genuine. .
Security consultant Adam Brown highlighted the risks, noting that such vulnerabilities could be exploited for malware distribution, or data and identity theft. He advised users to exercise caution when opening attachments, even from familiar sources.
To mitigate the risk, users should update their WhatsApp for Windows application to address the identified vulnerability and enhance the application's security.
https://www.theregister.com/2025/04/08/whatsapp_windows_bug/
HellCat Ransomware Exploits Stolen Jira Credentials to Breach Global Firms
In April 2025, cybersecurity researchers at Hudson Rock identified a series of cyberattacks by the HellCat ransomware group targeting four companies across the United States and Europe. The attackers exploited login credentials for Atlassian Jira, a popular project management tool, which were previously stolen through infostealer malware such as StealC, Raccoon, Redline, and Lumma Stealer. These credentials had been harvested from infected employee devices months or even years before the breaches occurred.
The affected organisations include Asseco Poland, HighWire Press (USA), Racami (USA), and LeoVegas Group (Sweden). HellCat posted evidence of the breaches on their leak site, threatening to release or sell sensitive data—including internal documents, emails, and financial records—unless their ransom demands are met.
This attack method is part of a broader trend where cybercriminals leverage stolen credentials from infostealer malware to infiltrate systems. Hudson Rock's data indicates that thousands of companies have Jira-related credentials exposed in such malware logs. Notably, even critical infrastructure entities like the FBI, Lockheed Martin, and Honeywell have been affected by similar tactics.
Organisations are advised to implement multi-factor authentication, regularly monitor for signs of infostealer infections, and promptly reset compromised credentials. Enhanced employee training on cybersecurity best practices can also help prevent such breaches.
https://hackread.com/hellcat-ransomware-firms-infostealer-stolen-jira-credentials/
Crypto Users Targeted by Sophisticated Node.js Malware Campaign Disguised as Binance and TradingView Installers
In April 2025, cybersecurity experts uncovered a malicious campaign exploiting Node.js (an open-source JavaScript environment) to target cryptocurrency enthusiasts. Attackers created hoax websites resembling popular platforms like Binance and TradingView, enticing users to download fraudulent desktop applications. Once installed, these applications deploy malware designed to harvest sensitive information and establish persistent access to victims' systems.
The malicious installers contained a dynamic-link library (DLL) named "CustomActions.dll," which collected system information using Windows Management Instrumentation (WMI) and set up scheduled tasks to maintain persistence. To avoid detection, the malware launched a legitimate-looking browser window displaying the actual Binance or TradingView website, masking its true intent.
Subsequently, the malware executed PowerShell commands to download additional scripts from remote servers. These scripts excluded the malware's processes and directories from Microsoft Defender scans, gathered extensive system data, and transmitted it to command-and-control servers via HTTPS. In some cases, the malware downloaded a Node.js runtime and a compiled JavaScript file to further its malicious activities.
An alternative infection method, known as ‘ClickFix’," involved executing inline JavaScript through PowerShell, enabling the malware to perform network discovery, disguise its traffic as legitimate Cloudflare activity, and modify Windows Registry keys for persistence.
This campaign highlights the evolving tactics of cybercriminals, who leverage trusted technologies like Node.js to bypass security measures and target unsuspecting users in the cryptocurrency sector.
https://thehackernews.com/2025/04/nodejs-malware-campaign-targets-crypto.html
Installers SAP NetWeaver Faces Critical Zero-Day Vulnerability Exploited in Ongoing Cyberattacks
In April 2025, European software company SAP disclosed a critical security flaw in its NetWeaver platform, identified as CVE-2025-31324, which cybercriminals have actively exploited. This vulnerability, carrying the highest severity score of 10.0, allows unauthenticated attackers to upload malicious files via the /developmentserver/metadatauploader endpoint, leading to unauthorised access and potential control over affected systems.
The exploitation involves uploading JSP web shells into specific directories, enabling persistent remote access, execution of arbitrary code, and data exfiltration. Some attackers have further deployed advanced tools like the Brute Ratel C4 framework to deepen their intrusion.
Security firms, including ReliaQuest and Onapsis, have observed that even systems with the latest patches were compromised, suggesting that the vulnerability was a zero-day exploit prior to its disclosure. The attacks have primarily targeted organisations using SAP NetWeaver, with a significant focus on the manufacturing sector.
SAP has released a security update addressing this vulnerability and advises all users to apply the patch immediately. Additionally, organisations are urged to inspect their systems for unauthorised files, particularly in directories like /irj/root, and to enhance monitoring for any signs of compromise.
This incident underscores the importance of timely patch management and vigilant security practices, especially for widely used enterprise platforms like SAP NetWeaver.
https://thehackernews.com/2025/04/sap-confirms-critical-netweaver-flaw.html
Infostealer Malware Exposes Tens of Thousands of Australian Banking Credentials
Between 2021 and 2025, at least 30,000 Australian banking passwords were compromised due to infostealer malware infections, according to cybersecurity firm Dvuln. These malicious programs infiltrated devices through deceptive emails, SMS messages, and online advertisements, harvesting sensitive data such as passwords, credit card details, and cryptocurrency wallet information. The stolen credentials, affecting customers of major banks including ANZ, NAB, Westpac, and the Commonwealth Bank, were often sold on the dark web, with some even offered as free samples to entice buyers.
While the majority of attacks targeted Windows-based computers, there has been a noticeable increase in mobile device infections. Dvuln emphasised that traditional security measures like multi-factor authentication (MFA) are not foolproof, as some advanced infostealers can bypass these protections by extracting authentication data. The firm advocates for a coordinated response involving financial institutions, government agencies, cybersecurity professionals, and the public to bridge the gap between device compromise and credential misuse.
The Australian Signals Directorate (ASD) has previously labelled infostealers as a "silent heist," highlighting their growing threat to national cybersecurity. They advise organisations, especially those allowing remote access or Bring Your Own Device (BYOD) policies, to be vigilant against such threats.
Globally, the Asia-Pacific region has seen a significant uptick in malware-driven data breaches, with Verizon reporting that such techniques were present in 83% of breaches in the region this year, up from 58% in 2024. Emails remain the primary vector for distributing various types of malware.
To mitigate risks, consumers are encouraged to keep their devices updated, use reputable antivirus software, and exercise caution when downloading or accessing online content.
https://ia.acs.org.au/article/2025/australians--banking-passwords-stolen-by-malware.html
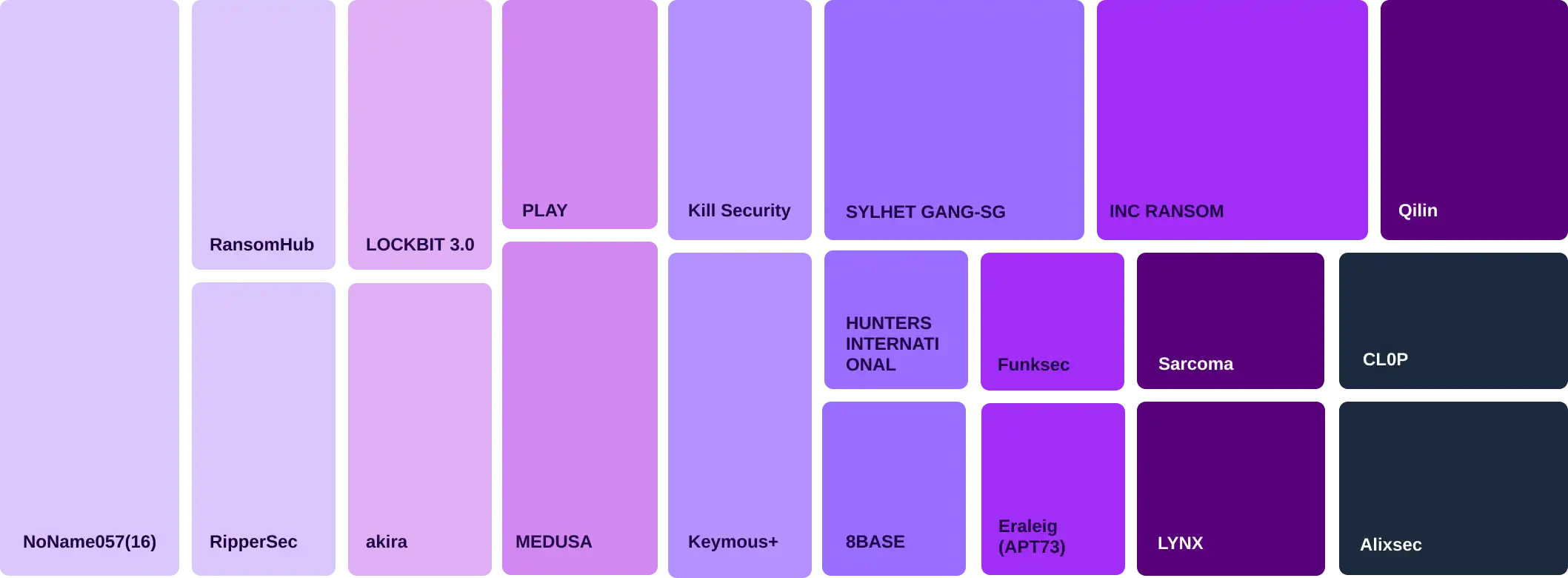
Threat actors targeting financial entities in April 2025
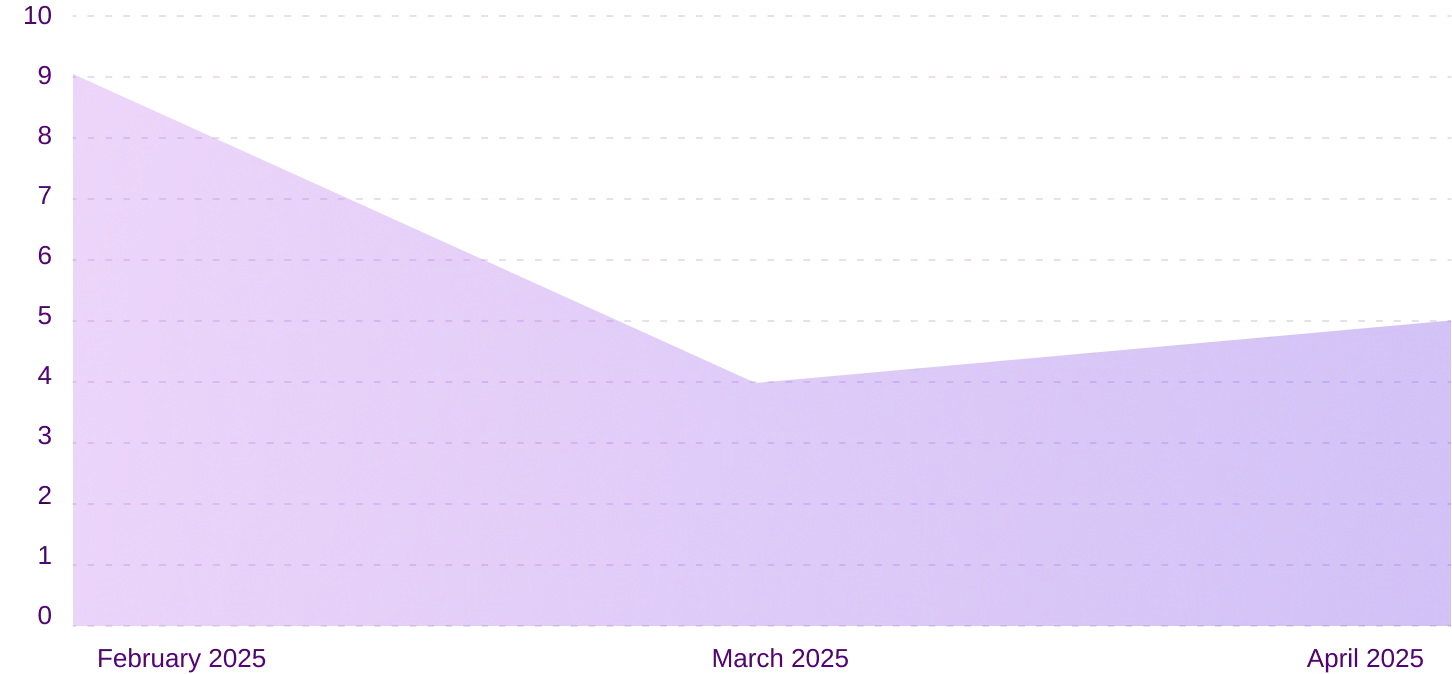
Ransomware vs Finance (last three months)

